WannaCry ''actualises'' the script of Terminator 2
John Connor who stopped the world cyber attack à la Skynet has turned out to be a simple British programmer
Tatarstan along with Chuvashia, as well as Nizhny Novgorod Oblast and Samara Oblast, has experienced problems the most due to the massive attack by hackers on May 12-13, Secretary of the Russian Security Council Nikolai Patrushev stated. The media reported that the virus WannaCry has affected 74 countries. Realnoe Vremya is investigating how this attack differs from all previous ones and who in Russia has suffered from its action.
About how WannaCry almost repeated the scenario from Terminator
The Friday's attack of crypto ransomware WannaCry began almost according to the scenario from the movie Terminator 2, when the virus Skynet infected computers around the world and eventually launched nuclear missiles. At least such thoughts arose among users of social networks when they saw the published map of the virus-infected countries.
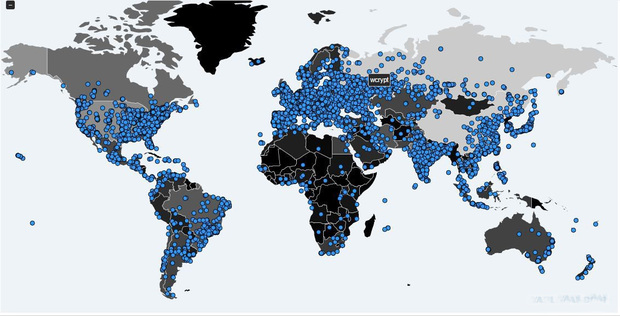
Trojan managed to hit more than 200,000 computers in over 150 countries. Among the countriesthe most affected were Britain and Russia. So, in the evening on May 12 from media reports it became known that the computers of the internal network of the Investigative Committee, as well as the computers of the Ministry of Internal Affairs of Russia underwent the hacker attack. Security officials denied this information. MefaFon mobile phone operator confirmed that the company computers had been hacked to Medusa news. On the same day, computers of hospitals located in different parts of the UK were attacked: users received a mail with the ransom demands. The computers of the telecommunications company Telefonica in Spain were also attacked.
Secretary of the Russian Security Council Nikolai Patrushev at a meeting on the issue of terrorism and migration ranked Tatarstan as one of the regions most affected by cyber attacks. Earlier, the Ministry of Information and Communications had stated that the state institutions in Tatarstan were not affected by the cyber attacks of the virus WannaCry.
By the way, The Times assessed how many users took the bait of the swindlers. The publication reported that the creators of the virus WannaCry earned more than $42,000.
Ordinary users around the world also suffered due to the virus. Computer users posted in social networks photos of their monitors that showed messages with a ransom demand (more often it was the amount of $300).

Who are you, John Connor of our time
But, according to the genre, for every Skynet there must be a John Connor. Indeed, in the world such person was found. A regular user from Britain Darien Huss can claim the role of the rescuer who managed to stop the attack. He wrote under the Twitter account MalwareTech.
After the beginning of the cyber attack, Darien Huss found the unregistered domain name sewn in the malware code where the requests were sent, reports The Guardian. He purchased this domain for less than $11 under the name iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. After that, he recorded thousands requests a second sent to him. Thus, domain registration suspended the operation of WannaCry.
Meanwhile, a programmer from Thailand Chanvit Caucasi together with colleagues from the Technology University of Suranari Plaza in Nakhon Ratchasima province created a program Block Wannacry able to block the virus. Experts shared the app on the Internet for free download, reports The Nation.
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.
— MalwareTech (@MalwareTechBlog) May 13, 2017
What beast is that
WannaCry is a crypto-virus, as well as exploit. Crypto-viruses, appearing on your computer, encrypt your data. As a result, the owner of the computer first can't open the files and then receives a message demanding a ransom in exchange for returning the access. The virus usually gets into your PC due to errors and negligence of users, a ''wrong'' click, downloading a questionable file, installing of extensions.
The exploit can be caught even making no mistakes because this type of malware exploits vulnerabilities in software. It can attack the computer when the user logs in the website that contains the malicious code, through spam or phishing mails, according to Kaspersky Daily. The trick is that the discovery of vulnerabilities by hackers, the release of an update with fixes takes time when unscrupulous individuals can attack.
Infection through local network
Kaspersky Lab claims that the creators of WannaCry used the exploit for Windows known as EternalBlue. It exploits the vulnerability that Microsoft closed in the security update MS17-010 dated 14 March 2017. Using this exploit, the attackers could obtain remote access to computer and install the exploit. It is noted that if the update was installed on the computer, its system cannot be hacked remotely. But if the exploit somehow still turned out to be on your computer, then the updates will not save you.
After WannaCry hacked computer, through local network it got on other computers of the network and began to scan them for the presence of vulnerabilities. For this reason, large companies whose computers are united by a local network suffered more than any other due to the attack.
Previously, Realnoe Vremya published about the main principles of safe behaviour for computer users.

Who did this?
Secretary of the Security Council of Russia Nikolai Patrushev stated that it is unsubstantiated to believe that someone's intelligence agencies are responsible for the cyber attack WannaCry, reports RIA Novosti. In his opinion, if it was the security services, the damage would be more serious. President Vladimir Putin expressed the opinion that the source of such actions is the US intelligence agencies, reports Interfax.
Prior to that, President of Microsoft Brad Smith said that behind WannaCry are CIA and NSA. The statement on the website of the corporation says that the United States in its own interests gather information about the vulnerabilities of software. Smith said that only developers should know about the vulnerabilities in Microsoft software, not the security services. He also called the incident a wake-up call and a signal for governments to awaken.
The Telegraph in its publication stated that the cybergroup Shadow Brokers had relation to the cyber attack. According to the newspaper, the associated with Russia hackers are taking revenge for US air strikes on Syria.
Among other versions who could be behind the global cyber attack, there are the North Korean hackers from the group Lazarus. Analysts of American Symantec and Russian experts of Kaspersky Lab came to such conclusion.